As businesses embrace remote work, SaaS sprawl, and bring-your-own-device policies, traditional Identity and Access Management (IAM) systems are becoming outdated. Legacy IAM tools struggle to enforce uniform access across fragmented cloud apps and hybrid devices. This growing challenge has led to a new paradigm in cybersecurity: Future Access Management (FAM).
But what exactly is Future Access Management, and how does it differ from traditional IAM solutions? More importantly, why is it essential in today’s threat landscape?
Let’s explore how FAM is helping organizations transition from reactive identity security models to context-aware, adaptive, and scalable access systems.
The Evolving Challenges in Access Management
Organizations today must address increasingly complex access scenarios due to:
1. Hybrid Work Environments
The boundaries between personal and corporate devices have blurred. Employees connect from coffee shops, home networks, and international locations forcing IT teams to protect assets beyond the perimeter.
2. SaaS Proliferation
Cloud-first companies rely on dozens, sometimes hundreds, of SaaS apps. These platforms are hosted across various vendors and regions, further complicating centralized access control.
3. Credential-Based Attacks
Credential stuffing, phishing, and privilege escalation are among the most exploited vectors today. Cybercriminals target centralized login credentials, making reactive IAM systems a weak link in the security chain.
The modern enterprise landscape requires access tools that are faster, smarter, and contextually aware.
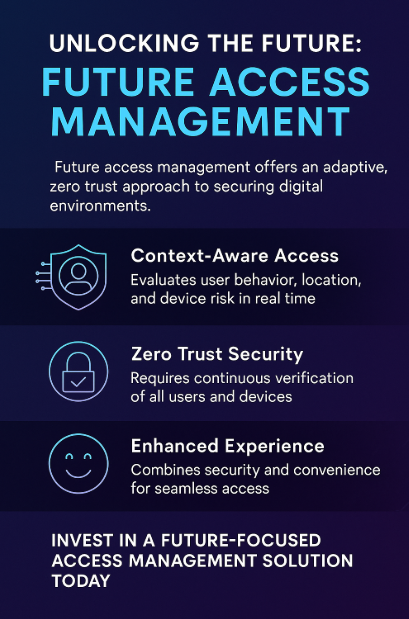
What Is Future Access Management?
Future Access Management refers to the new generation of cybersecurity frameworks that go beyond static credentials and role-based access. It integrates machine learning, contextual data, and automation to assess and respond to access requests dynamically.
Here’s how it works:
Context-Aware Decisions
FAM platforms evaluate user behavior, location, device security posture, and time of access to determine risk in real time. For example, an employee logging in from a known device at 9 a.m. may be granted seamless access, while the same request from an unrecognized device in a foreign country triggers multi-factor authentication or a block.
Zero Trust Implementation
Rather than assuming internal traffic is safe, Zero Trust assumes nothing is safe by default. Every user and device must continuously prove trustworthiness, whether inside or outside the corporate network. FAM solutions automate this validation, minimizing manual approval workflows.
Frictionless Experience
Older IAM systems often degrade UX with constant reauthentication. FAM platforms strike a balance—enhancing security without frustrating users. Seamless, conditional access allows productivity without compromising safety.
Benefits of Future Access Management
Implementing FAM transforms your cybersecurity architecture in measurable ways:
-
Reduced Risk of Insider Threats & Lateral Movement
Contextual access narrows exposure from compromised accounts. -
Enhanced Compliance and Auditing
Automated logging, anomaly detection, and access trails support compliance with GDPR, HIPAA, and SOC 2. -
Improved Operational Efficiency
IT teams spend less time managing tickets and resetting passwords. Users experience fewer login issues and downtime. -
Scalable Across Hybrid/Remote Teams
Whether your workforce is remote-first or global, FAM scales without needing on-prem infrastructure.
Use Case Snapshot: A Global SaaS Firm
A mid-sized SaaS company with 500 employees recently transitioned to Future Access Management. Within 60 days, they reported:
-
40% reduction in help desk tickets related to login issues
-
70% improvement in threat detection speed via contextual AI triggers
-
Full compliance readiness for ISO 27001 and SOC 2
-
Increased workforce productivity due to reduced access friction
What This Means for You
Whether you’re an IT security officer, CISO, or business leader, implementing FAM is no longer optional it’s a strategic necessity.
If you want to:
-
Proactively detect access-based threats
-
Deliver a secure yet smooth user experience
-
Adapt to a fast-evolving, decentralized digital environment
Then it’s time to invest in a solution that supports adaptive authentication, policy automation, and continuous access evaluation.
The Future Is Now
Future Access Management is not just a trend it’s the cornerstone of modern enterprise cybersecurity. As remote work grows and cyber threats evolve, organizations that adopt proactive access strategies will thrive. Those who cling to legacy IAM tools risk being left behind.
Whether you’re in fintech, education, healthcare, or SaaS, this is your chance to reimagine access as a business enabler not just a security control.
Final Thoughts
Cybersecurity is evolving at the pace of innovation and so must your approach to identity and access. Future Access Management represents a significant step forward: context-driven, zero trust-based, user-friendly, and highly scalable.
Now’s the time to ask: Is your organization ready for the future of access?







